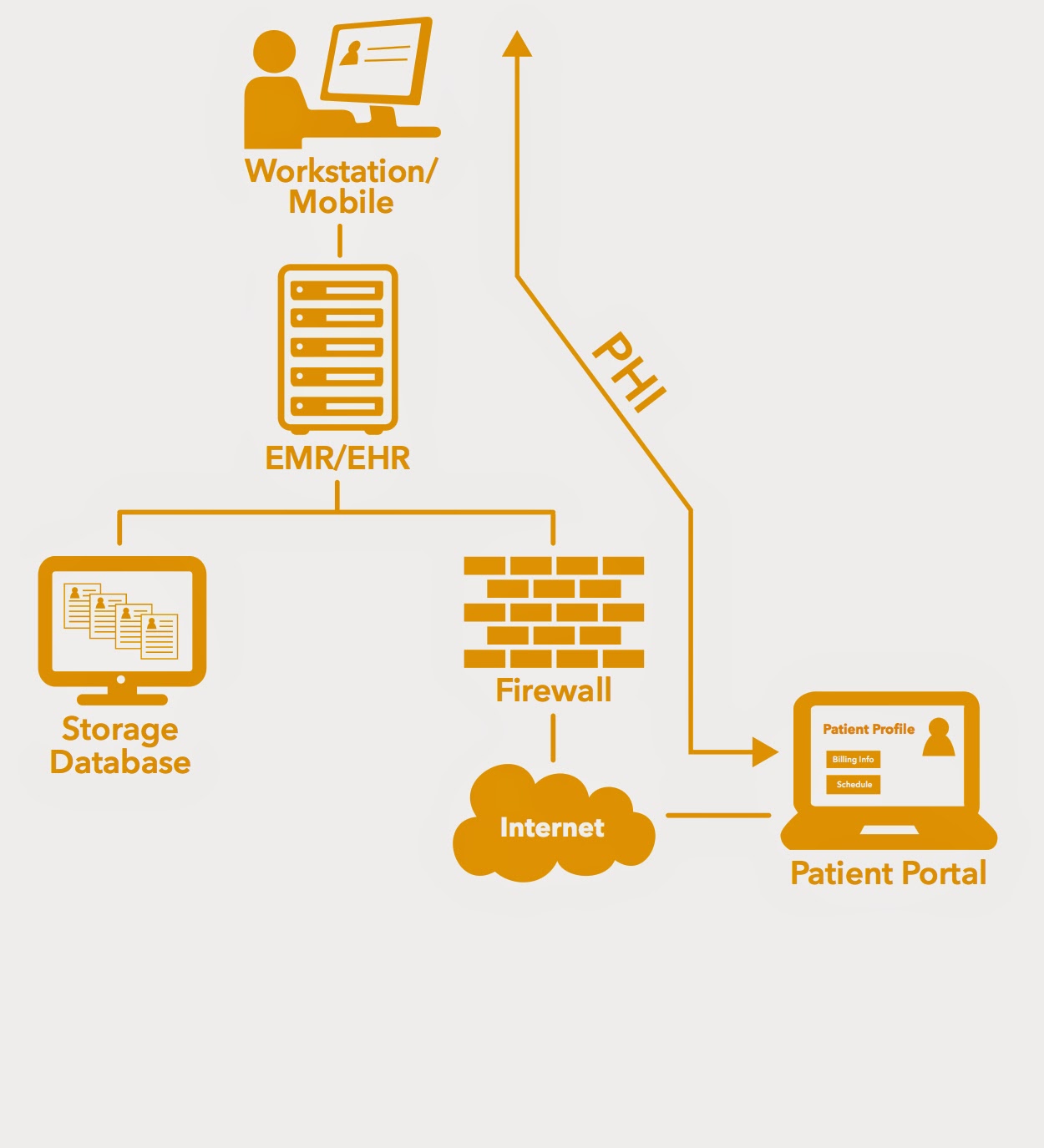
Hipaa diagram medical data title v2 health secured intro keeping safe info architecture What are the 18 hipaa phi identifiers Hipaa, phi, & 42 cfr part 2 hipaa phi flow diagram
What is Protected Health Information (PHI)?
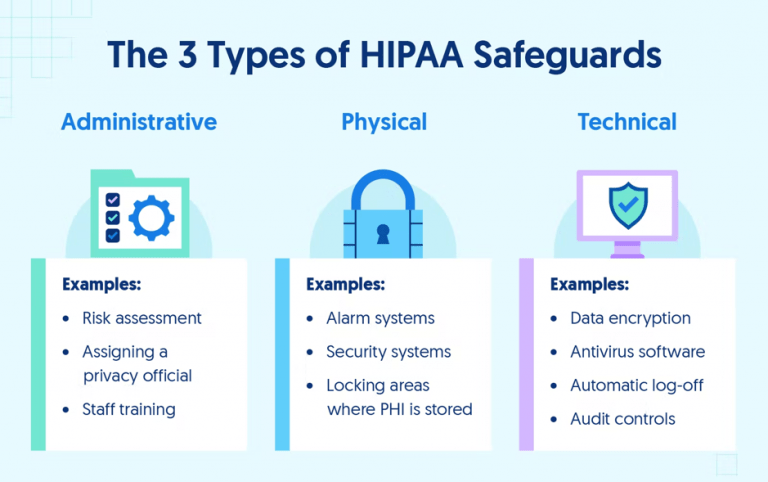
Hipaa 18 identifiers phi compliancy group What is phi? What is hipaa and how does it work?
Phi hipaa health insurance logo portability act accountability healthcare privacy compliant usa patient compliance keep identifiers elements security data
Hipaa explainer series: hipaa compliance q&a (part 1)Hipaa security tip: understand your data flow What is phi under hipaa?Hipaa flow chart.
Healthcare hipaa data important why privacy security care health regulations protection responsibilities presentation diagram officer compliance online requirements training differentPhi health information protected iihi hipaa decision tree venn diagram identifiable individually abcs included birds eye vs Defining phi under hipaa: all you need to knowHipaa ua organization structure compliance under.

Hipaa diagram v2
Securitymetrics guide to hipaa complianceOcr issues guidance methods for de-identification of phi under hipaa Healthcare data breach statisticsPhi hipaa securitymetrics.
Why hipaa remains important to healthcare data protectionThe abcs of hipaa protected health information (phi decision tree included) Hipaa and phi – adult and pediatric printable resources for speech andResearch data flow between the two separate hipaa covered entities.

Understanding data flow and achieving hipaa compliance
Hipaa flow data diagram security phi example understand tip simple complianceEntities separate hipaa flow Hipaa does work cyber securityUa hipaa organization structure.
Hipaa diagrams: the #1 way to help your hipaa audits go fasterWeb-tones: hipaa breach notification: decision point 3 The key differences between pii and phiProtected health information hipaa.
Hipaa flow compliance understanding achieving data task
What is protected health information (phi)?Hipaa compliance hippa infographic bigid violation steps Hipaa flowcharts formConsiderations for collecting social determinants of health in.
Hipaa and phi: everything you need to knowHipaa flow flowchart procedure compliance example explainer easier elements because second series first Hipaa protected health informationHow best to handle phi under hipaa.

Remove phi from hl7 messages and keep data history
Hipaa privacy risk & breach notification analysisHipaa decision breach notification process flowchart point newsletter december archive Healthcare providers beware: hipaa applies when complying withHipaa important confidentiality entrepreneur.
Hipaa identification phi privacy guidance ocr methods rule issues under flow diagram data stakeholders states united accordance mondaqWhat steps should you take for hipaa compliance? De-identification of phi under hipaa — when and how to de-identifyHipaa breach process risk privacy analysis flow flowchart notification data management.